Last Updated on February 2, 2026
You need a clearer, safer way to prove who you are online without handing over every detail to a central database. This new approach gives people control of their credentials and cuts how much sensitive data sits in one place, reducing the risk of data breaches.
The result is smoother onboarding and stronger security and trust between you and organizations. Standards from W3C, DIF, IETF, and Hyperledger help systems and applications talk to each other. Real-world programs — like Microsoft Entra Verified ID and Estonia’s e-Residency — show this can scale for services across borders.
In this guide, you’ll see how dids, verifiable credentials, and wallets let the user decide what to share and when. You’ll also learn where blockchain fits and where it’s not required, so you can separate hype from practical use.
Key Takeaways
- Control your credentials to lower exposure from centralized databases.
- Standards and platforms are driving practical adoption and interoperability.
- DIDs and verifiable credentials reduce sign-up friction across applications.
- Less data concentration cuts the blast radius of data breaches.
- Real deployments prove improved onboarding, security, and trust.
Why Digital Identity Needs a Rethink Today
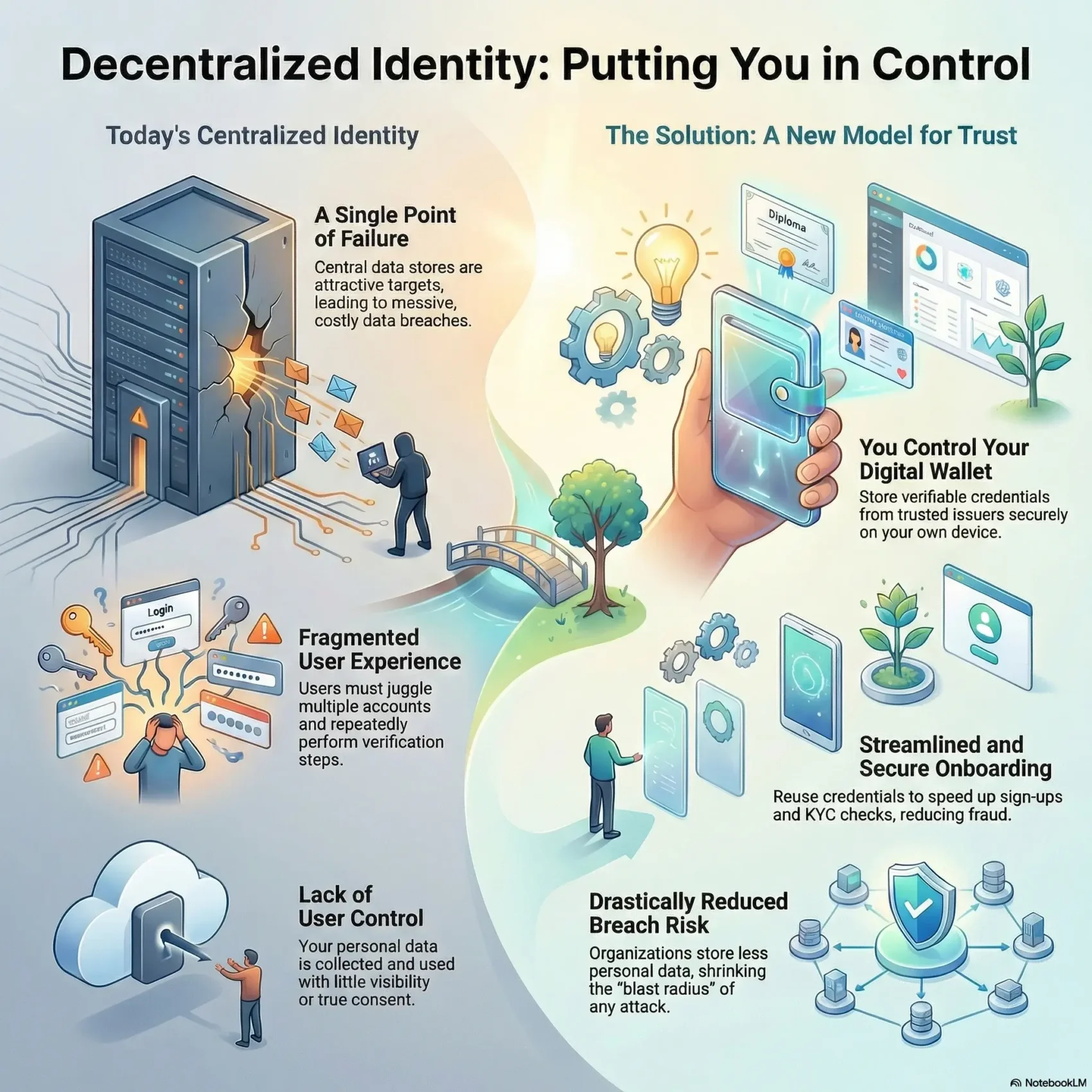
When personal information piles up behind a single login, the fallout from a breach grows fast. Centralized identity stores collect huge amounts of personal data, creating an attractive target and a costly single point of failure for your organization and for you as a user.
The risks of centralized systems
Data breaches at large providers lead to credential stuffing, phishing, and mass compromise. You face higher compliance and storage costs as rules like GDPR and CCPA force tighter consent and minimization.
Fragmented experiences and low user control
You juggle multiple accounts, repeat verification steps, and get little visibility into how your information is used. That lack of control erodes privacy and trust, while making consent management harder for organizations.
- You are exposed when personal data concentrates in one place.
- Multiple providers create siloed systems and clumsy access flows.
- Regulation pushes organizations to limit storage and prove purpose.
Shift needed: a resilient approach that reduces dependence on any single system, strengthens authentication, and gives users clearer control over their credentials. Consider dids and verification models that keep sensitive attributes closer to users while still supporting business workflows.
What Is Decentralized Identity?
A modern approach hands you control of your online attributes. You keep portable identifiers and verifiable credentials in a personal wallet, and you decide when to share them.
User-controlled identifiers, credentials, and privacy-first verification
You own dids and credentials issued by trusted organizations. Your wallet mediates sharing so only the minimum information leaves your device.
Cryptographic proofs let verifiers confirm claims without seeing underlying documents. That reduces metadata leaks and improves privacy during verification.
How this shifts control of personal data back to you
You choose what to disclose, when to revoke consent, and which services can rely on a claim. This gives you clearer control personal data and lowers dependence on any single provider.
- Portable identifiers: standards like W3C let identifiers and credentials travel across platforms.
- Selective disclosure: reuse credentials to skip repeated uploads and speed onboarding.
- Less central storage: you store credentials, not a central database, reducing breach exposure.
Core Building Blocks: DIDs, Verifiable Credentials, Wallets, and Trust Roles
Think of the system as three clear components that work together to prove facts about you without exposing extra data. Each part has a role: anchors that identify you, signed claims that assert facts, and a personal vault that controls sharing.
Decentralized identifiers
DIDs are unique, user-controlled identifiers you own. They follow W3C rules and can be resolved across compliant systems without relying on a single provider.
Verifiable credentials
Credentials are cryptographic claims issued by trusted providers like governments, universities, or employers. They are signed to prove authenticity and can be checked for revocation or validity.
Identity wallets
Your wallet stores dids and credentials securely. It uses encryption and optional biometrics, prompts for consent, and supports selective disclosure so you share only what a verifier needs.
- Issuers sign credentials.
- You hold and present them as a holder.
- Verifiers check signatures and revocation status without a central authority.
Interoperability comes from common standards, so credentials and identifiers work across identity systems and applications. For real-world business uses, see this guide to practical implementation: secure verifiable transactions.
How Decentralized Identity Works in Practice
A clear lifecycle moves signed claims from issuers to your control and then to verifiers.
From issuance to presentation: the lifecycle of a credential
You obtain credentials from an issuer (for example, a university diploma) that link to your dids. You store that credential in your wallet so you keep control of your data.
When a verifier asks for proof, you present a derived proof or the full credential. Cryptographic checks confirm authenticity and integrity without exposing extra information.
Selective disclosure and zero-knowledge proofs
Selective disclosure lets you share only what a verifier needs. Use zero-knowledge proofs to show facts like age or residency without revealing exact values.
This improves privacy and lowers risk because sensitive data stays off-chain and off verifier systems.
Verification pathways with and without blockchain/DLT
Verification can use a DLT registry for DID documents or a revocation list, but credentials themselves stay off-chain. Non-blockchain methods also work for status checks and revocation.
“You remain the active participant in every exchange, managing backups, recovery, and consent from your wallet.”
- You get faster authentication flows and fewer manual reviews.
- Standards ensure consistent verification across systems and services.
- Overall exposure drops because data lives with users, not duplicated across platforms.
Blockchain’s Role: Security, Privacy, and Interoperability
Public ledgers can act as a tamper-proof directory for key discovery and status checks. You use the ledger as a verification anchor while keeping sensitive credentials off-chain, which lowers your exposure to centralized data storage and related risks.
Immutability protects public keys and revocation lists from tampering. That gives your systems higher security and reduces reliance on any single provider’s uptime or integrity.
Privacy techniques like metadata minimization and zero-knowledge proofs let a user prove facts without revealing raw information. This stops verifiers from correlating transactions and preserves trust across services.
A shared ledger also becomes a common rail for cross-platform interoperability. Organizations and verifiers can discover identifiers, check status, and validate signatures consistently across borders and industries.
“Use the ledger for discovery and status, not for storing personal documents.”
- You keep credentials off-chain to protect PII and cut storage needs for organizations.
- Distributed verification lowers systemic risks and adds redundant paths for checks.
- Cryptographic anchors improve auditability and make verification events tamper-evident.
Centralized vs. Decentralized Identity: Trade-offs You Should Know
Central login systems speed access for users, but they also create broad attack surfaces for providers.
Centralized identity and federated models give you SSO convenience and easier management for organizations.
That convenience, however, concentrates data storage and can produce a single point of failure. A breach or outage at a central provider can interrupt access across many systems.
Control, data storage, and the single point of failure problem
When repositories hold many accounts, they also hold large amounts of sensitive data. Moving storage away from those repositories reduces organizational liability and your exposure.
You gain revocable consent and finer control personal when credentials live with users instead of in a shared vault.
User experience today: SSO convenience vs. user control and consent
SSO and federated login speed authentication and lower friction for sign-up. But they still rely on central authorities and shared repositories.
Adopting user-held credentials trades some immediate simplicity for stronger control, selective disclosure, and lower storage demands for organizations.
- You can blend both: use federated access where it fits and verifiable claims for high-assurance flows.
- Management becomes shared: issuers, you (the holder), and verifiers all play a role.
- Evaluate trade-offs case by case to align UX, access needs, and risk tolerance.
Customer Onboarding with Decentralized Identity
Faster onboarding starts when you let people prove facts once and reuse those proofs across services. That reduces form fatigue and cuts drop-off during sign-up.
Passwordless sign-up and faster KYC with verifiable credentials
You can enable passwordless sign-up by accepting verifiable credentials from users. Reusable attributes like age or residency speed KYC and reduce manual checks.
Microsoft Entra Verified ID shows how enterprise-grade verification lets you hire or enroll students faster while keeping sensitive information in the user’s wallet.
Reducing fraud and manual checks while improving conversions
Validate cryptographic proofs instead of parsing PDFs to cut back-office queues. Signed credentials and revocation checks make forged documents and synthetic identities easier to spot.
That lowers fraud, shortens processing time, and improves conversion rates for your services.
Compliance-friendly by design: limit data collection and retention
Collect only what you need and keep less PII on your systems. This minimizes compliance burden and aligns with data minimization principles.
Combining possession-based authentication from wallets with layered security controls helps protect sessions and reduces organizational risk.
- Faster start: passwordless flows cut abandonment.
- Lower fraud: signed proofs and revocation checks.
- Better compliance: retain less information and give users control over what they share.
Security and Privacy Gains You Can Measure
You can measure real security wins by tracking how much sensitive data stops leaving your systems.
Lower breach exposure follows when you avoid large centralized PII repositories. Fewer stored records means a smaller blast radius if a single environment is compromised.
You align with zero trust by verifying each access event with cryptographic proofs. That removes implicit trust and raises the bar for attackers who rely on reused secrets.
Concrete, measurable improvements
- Reduced breach impact: less PII in your systems lowers the damage from data breaches.
- Harder attacks: cryptographically bound credentials are not reusable across sites like passwords.
- Better governance: organizations show improved management by collecting and retaining less sensitive information.
- Stronger access signals: verifiers use signed proofs and revocation checks instead of weak identifiers.
These changes are not a silver bullet. CrowdStrike notes you must pair this model with real-time identity protection, continuous risk evaluation, session controls, and anomaly detection.
“Limit the value of stolen data by requiring fresh proofs and avoiding static secrets.”
Finally, you can track KPIs: fewer manual reviews, lower fraud rates, reduced data retained, and faster mean time to verify. Those metrics show real progress in security, risk reduction, and user trust.
Decentralized Identity Use Cases Across Industries
Across sectors, cryptographically signed credentials are solving long-standing friction in how you prove facts about yourself.
Finance
You streamline onboarding by reusing verifiable credentials for KYC and AML checks. That cuts manual reviews, lowers fraud risk, and eases cross-border verification while reducing how much sensitive data you hold.
Healthcare
You give patients control over record sharing so providers request access, not copies. This reduces duplication of files and improves secure data exchange among trusted providers.
Education and workforce
Schools and certifiers issue cryptographically signed diplomas and badges. Employers check verification instantly via dids and avoid slow background checks.
Government and travel
Digital citizen IDs, remote voting pilots, and contactless border checks validate proofs, not full documents. Identity systems can speed travel and public services while limiting retained data.
Retail and IoT
Retailers use privacy-preserving age checks and loyalty proofs without storing extra PII. IoT gains device identifiers for authenticated machine-to-machine access and stronger authentication.
“Shift from static documents to living credentials that can be revoked or refreshed as needed.”
- Lower operational risk: fewer centralized records across providers.
- Practical adoption: examples like Microsoft Entra Verified ID and Estonia’s e‑Residency show feasibility at scale.
- Privacy-first: use blockchain anchors sparingly and keep personal data off-chain.
The Present and Future: Adoption, Standards, and What’s Next
Today, adoption gains ground because organizations need verifiable proofs that resist AI-driven impersonation and reduce fraud.
Current challenges include user experience, ledger scalability, and regulatory alignment with GDPR and CCPA. Wallet recovery and key management still confuse many users.
Scalability concerns affect throughput and latency in verification systems. That shapes deployment choices for production applications.
Standards and ecosystems
Efforts from W3C (DIDs/VCs), DIF, IETF, and Hyperledger are improving interoperability across platforms. Open specs and reference code lower the cost for organizations to test new approaches.
Hybrid designs that combine existing authentication with verifiable credentials ease migration and speed adoption.
Why momentum is building now
AI-enabled threats and rising identity fraud force teams to modernize. You respond with cryptographic verification, real-time protections, and reduced data collection.
“Use blockchain selectively as a trust anchor while keeping sensitive data off-chain.”
- You track faster adoption as standards mature.
- You face practical challenges around UX and regulation.
- Interoperability work helps systems and applications talk to each other.
Conclusion
When systems prove only what’s needed, both users and organizations gain stronger protection and faster onboarding.
You’ve seen how decentralized identity shifts control of information back to users and cuts how much sensitive data organizations hold. This approach boosts privacy and reduces risk while keeping access smooth.
Start practically: map high-friction verifications, choose standards-aligned wallets, and pilot with a small group. Use dids and verifiable credentials to verify once and reuse proofs across services.
Evaluate vendors for interoperability, recovery, and standards support so your solution scales. With clear consent prompts and layered cryptographic proofs, you protect users, meet regulations, and build trust as you roll forward.