Last Updated on December 13, 2025
This article gives a clear, practical view of how the regulation affects your SaaS roadmap when outputs touch EU markets or users.
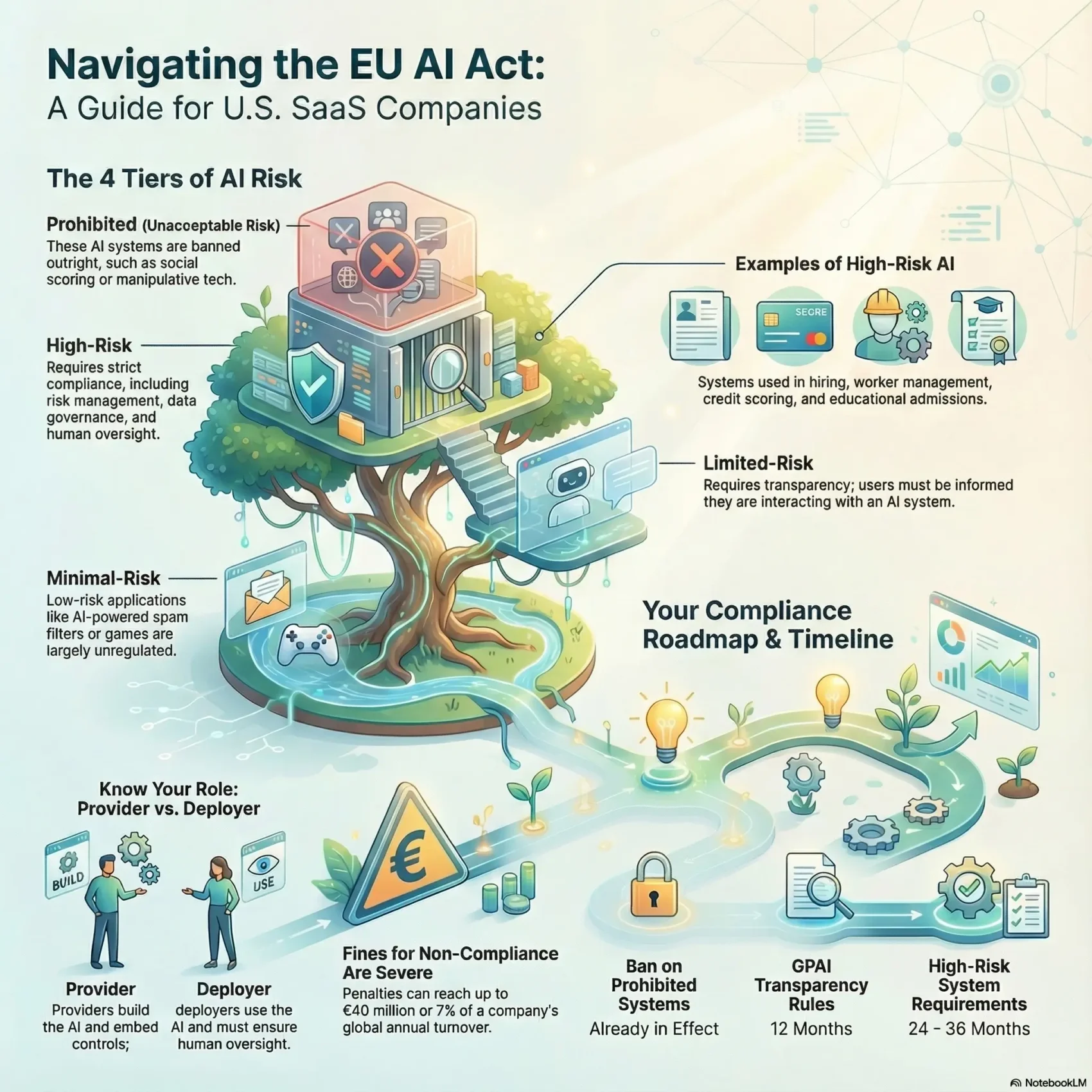
We’ll unpack what “risk-based” means for your systems, models, and providers. You’ll learn which systems are prohibited, which are high risk, and what limited or minimal risk looks like for product teams.
Expect a concise list of obligations and requirements for providers versus deployers, plus a timeline for staged applicability so you can plan training, documentation, and data work without guessing.
We also point to the european commission, national authorities, and practical tools you can use to map scope, track updates, and build safety into your technology and website pages.
Key Takeaways
- Scope reaches you when your system outputs are used in EU markets or by EU users.
- Risk tiers—prohibited, high, limited, minimal—drive what actions you must take.
- Providers and deployers have different obligations; map responsibilities early.
- Use available tools and official information to align training and documentation with deadlines.
- Translate legal requirements into product checklists to reduce operational risk.
Why the EU AI Act matters to your U.S. SaaS right now
If your system delivers outputs to European users, the rules change how you design, test, and disclose features. Your product may be subject to a tiered risk framework that assigns duties based on the harm potential of each application.
Risk-based framework in a nutshell:
- Unacceptable: Certain systems are banned outright.
- High-risk: Requires risk management, data quality, documentation, oversight, accuracy, and transparency.
- Limited: Transparency duties (for example, chatbots must disclose they’re generated).
- Minimal: Low-risk uses like games or spam filters are largely free to operate.
Extraterritorial scope means you fall into scope when your system’s outputs reach the market or are used by EU users, even if your company is based in the United States.
- Map systems and models by function: employment, education, access to services often flag as high-risk.
- Document what data and training sources you used and how users receive information about AI-generated content.
- Assign provider vs. deployer obligations early and train product, engineering, and legal teams together.
Start with tools like the official text explorer and an Act Compliance Checker to scope risk, track obligations, and plan implementation across your website and products.
Key implementation dates you can’t miss
Timelines now matter: some bans are already in effect and other obligations roll out on fixed clocks. You should align product milestones to avoid surprises and enforcement exposure.
Present timeline: bans and phased applicability
The ban on unacceptable risk systems began on February 2, 2025 under Regulation (EU) 2024/1689. Remove or redesign any prohibited functionality now to limit enforcement risk.
High-risk systems vs GPAI systems: clocked deadlines
GPAI transparency rules start a 12‑month window for disclosures, copyright checks, and training‑data summaries for models you operate.
High‑risk requirements kick in at 24 months for Annex III systems and 36 months for Annex I product contexts. Use this time to build risk management, human oversight, and lifecycle records.
Codes of practice and standards: staged milestones
Codes of practice apply nine months after entry into force. European standardization bodies will develop harmonized standards during implementation, giving you pathways to meet technical requirements.
- Lock roadmap to real dates and remove prohibited features immediately.
- Start 12‑month tasks for transparency now if you touch GPAI models.
- Create internal go/no‑go milestones tied to each phase and use a tool to track progress across teams.
Scoping your AI system: are you high-risk, limited-risk, or out of scope?
Scope starts at decision points. If your system affects access to services, employment, education, or legal outcomes, treat that flow as a potential high-risk application and scope it accordingly.
Prohibited applications to avoid. Exclude manipulative behavior‑shaping, social scoring, and biometric categorization that infers sensitive traits. Do not use untargeted facial scraping, emotion recognition in workplaces or schools (unless strictly medical or safety related), or profiling that predicts criminality without human context.
Annex III use cases and SaaS examples
Annex III flags systems used for hiring (candidate screening), worker management, admissions, testing, proctoring, and access to essential services like credit scoring. If your SaaS automates these tasks, assume high risk.
- Document whether a function is only a narrow procedural step or preparatory task; narrow carve‑outs can reduce obligations but must be recorded.
- If profiling appears in any Annex III area, plan for full requirements: governance, documentation, and oversight.
- For limited‑risk applications (chatbots, generated content), meet transparency duties so users know when they interact with an artificial intelligence application.
Map your data flows and label the system components, models, and data that create risks. Use a scoping tool and internal checklist early so providers and teams align on requirements before you ship.
EU AI Act compliance obligations for SaaS providers and deployers
Start by mapping who does what: providers must embed risk controls, while deployers translate those controls into everyday user safeguards. This split keeps development work focused and makes operational duties clear.
Provider requirements and development practices
As a provider, build a living risk management program tied to your product lifecycle. Implement a quality management system and add threat models, tests, and documented sign‑offs to engineering sprints.
Your data governance must prove datasets for training, validation, and testing are relevant, representative, and error‑controlled. Store evidence in a technical file that includes model evaluation, architecture, and controls.
Operational safety, records, and downstream use
Design automatic record‑keeping to log events and substantial modifications across the lifecycle. Engineer for accuracy, robustness, and cybersecurity with measures that reference standards.
Deployer responsibilities and user protections
As a deployer, provide AI literacy for operators and users, run fundamental rights impact assessments where required, and add human oversight that fits real workflows. Make escalation paths and correction mechanisms explicit so users can challenge or fix decisions.
- Insert privacy and security checkpoints during development.
- Make instructions for use clear and actionable for downstream users.
- Track implementation with clear responsibilities and audit-ready records.
General-purpose AI models, systemic risk, and your product roadmap
When your models serve many users across borders, transparency and extra testing become non-negotiable parts of your roadmap.
Transparency and copyright: disclosures, training data summaries, and law
Publish a clear training summary that lists text and media sources used to train models. Respect copyright and disclose when content is generated by artificial intelligence.
Providers must include technical documentation and downstream information so integrators know limits and safe uses.
Systemic risk thresholds and obligations
A model trained with very large compute—roughly at or above 10^25 FLOPs—is presumed systemic. If so, providers must notify the european commission within two weeks.
Systemic-risk duties include model evaluations, adversarial testing, incident reporting, and robust cybersecurity. Treat these as ongoing product work, not one-off tasks.
Open models, codes of practice, and cooperation
Open and free-license models still must respect copyright and publish training summaries unless they present systemic risk.
- Build information packages for downstream teams that explain capabilities, limits, and safe use.
- Consider following a code of practice to show good faith while harmonized standards appear.
- Keep evidence that your provisions act obligations and evaluations are active in production.
For practical steps and integration help, review a concise model integration guide so downstream partners can meet their obligations providers expect and reduce market friction.
Data, transparency, and human oversight: turning law into product and policy
Turn regulatory text into product features by treating data and user notices as core UX elements, not afterthoughts. That mindset helps you build systems that meet obligations and respect user rights.
Data governance in the real world: relevance, representativeness, and error controls
High-risk providers must set dataset gates: define relevance, test representativeness, and run error checks before each release.
Put measurable checks in your system design docs and automate validation so issues surface in development, not after launch.
User disclosures and content labeling: chatbots, deepfakes, and website UX
Place clear, in-context disclosures at chatbot entry points and on content pages. Label generated or modified content so users know what they see.
Make labels consistent: reuse badges and notices across your website and help page to reduce confusion and speed implementation.
Designing human-in-the-loop oversight without breaking workflows
Define when humans must review or override and what evidence they get. Train staff on these flows and capture oversight actions as audit data.
“Human oversight works best when it fits real job roles and feeds back into training without creating new risk.”
- Document provider vs deployer responsibilities in runbooks.
- Align training for product, engineering, and support teams on disclosures and rights requests.
- Treat transparency, training, and oversight as ongoing implementation work and iterate from user feedback.
Enforcement, penalties, and support from authorities
Enforcement mechanisms will shape how you prioritize fixes, disclosures, and incident responses across your product lines. You need a clear plan for handling investigations, user complaints, and regulatory requests.
Penalties tiers: prohibited practices, transparency/data violations, other non-compliance
Penalties scale with severity. Prohibited practices can lead to fines up to €40M or 7% of worldwide turnover.
Transparency and data governance breaches may reach €20M or 4% of turnover.
Other non‑compliance can trigger fines up to €10M or 2% of turnover.
The EU AI Office and national authorities: supervision, evaluations, and complaints
The EU AI Office coordinates oversight for general‑purpose models and can evaluate systemic risk.
National authorities supervise most systems, handle complaints from users, and request evidence from providers.
SME measures, sandboxes, and standards to reduce burden
Small and medium firms get practical support: priority sandbox access, guidance, and lower conformity fees.
- Track evolving standards and adopt recognized measures to reduce review time.
- Build an enforcement playbook: who responds, what documents to supply, and remediation steps.
- Provide targeted training for complaint handling, rights responses, and tool use.
Practical tip: align your implementation timeline with enforcement risks and keep market communications honest to limit escalation.
Conclusion
Start by naming owners and setting short timelines for documentation, testing, and oversight across your product lifecycle. ,
Center your program on providers’ and deployers’ core obligations, then tailor work to the specific risks your systems and models pose.
Prioritize practical enablement: training for teams, tighter development checks, and clear content on your customer page about how your system works in the market.
Treat the implementation act window as an opportunity to iterate: small, steady updates beat last‑minute fixes. Keep open lines with authorities and use sandboxes and standards to reduce friction.
Above all, anchor decisions in user safety and rights—good governance lowers risks and makes your product stronger.