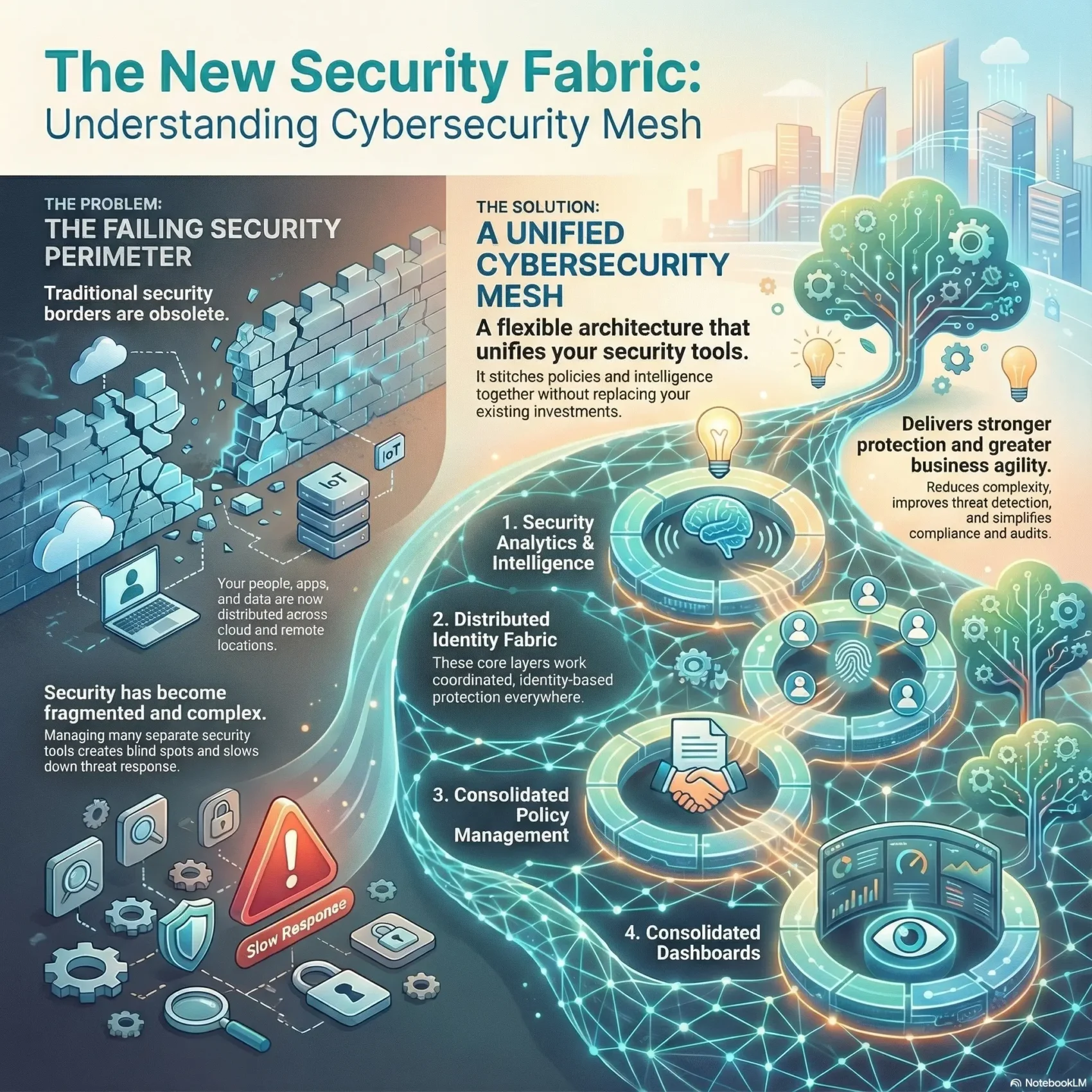
This introduction helps you see why a modern security approach matters now. As work shifts to cloud, edge, remote, and IoT locations, the old perimeter no longer protects your data and assets. You need a way to unify controls without ripping out best-of-breed tools.
Think of the mesh as a composable architecture that stitches policies, identity, and intelligence across distributed environments. It lets your organization respond faster to threats while keeping existing investments working together.
Gartner frames this concept as scalable and interoperable. With cybercrime costs rising into the trillions and attacks like phishing and ransomware increasing, an integrated approach offers real benefits: better visibility, stronger protection, and more efficient operations.
Key Takeaways
- The mesh concept unifies security across dispersed environments without full replacements.
- A composable architecture helps you stitch policies and intelligence across tools.
- It focuses on identity and shared context rather than static network borders.
- Adopting this approach improves visibility, protection, and operational efficiency.
- Market trends and rising attack costs make this architecture essential for enterprises.
What Is Cybersecurity Mesh and Why It Matters Now
Modern risk comes from fragmentation — and the right architecture stitches visibility and control back together.
Cybersecurity mesh defines a composable, scalable way to unify diverse security capabilities into a coordinated whole. It uses shared policy, identity, and analytics to let tools interoperate without replacing every platform you already run.
Perimeter-era thinking assumed apps and users lived inside a fixed border. Today your people, apps, and data span cloud services, SaaS, and remote sites. Static controls struggle to keep up.
A composable, scalable approach to unify assets
This model reduces operational complexity by centralizing governance while letting local tools enforce policies. Consistent controls cut duplicated effort and misalignment.
“A coordinated fabric of identity and intelligence helps you detect and respond faster across hybrid environments.”
From perimeter-based security to an identity- and policy-driven mesh
The architecture counters risks from hybrid cloud and distributed assets with shared intelligence and consolidated management. You can integrate what you have, standardize policies, and evolve without wholesale replacement.
- Centralized visibility across many platforms.
- Reduced duplication and faster response.
- Gradual adoption that preserves existing investments.
For a practical look at how this approach supports edge and distributed operations, see this primer on edge-driven architectures.
cybersecurity mesh architecture Explained for Today’s Distributed Environments
Today’s enterprises run services and users across dozens of platforms, so your security design must follow them rather than expect them to stay put.
How mesh supports hybrid multicloud, remote work, edge, and IoT
A modern mesh follows identities and data across Microsoft 365, Google Workspace, Salesforce, and public cloud services. That means protections travel with users whether they are on VPN, at home, or on the road.
Shared intelligence links detections from email, web, endpoint, and network so a threat in one domain triggers protections in others. Edge and IoT devices join the fabric through identity checks and posture validation.
Solving security sprawl: centralized policy with tool interoperability
Centralized policy gives you one source of truth while letting native security tools enforce controls locally. That preserves the strengths of each platform and reduces duplicated work.
- Consistent policy across cloud and on‑prem systems
- Interoperability so tools share signals and act in unison
- Fewer portals to manage and faster, prioritized response
“A single policy layer with shared analytics turns scattered alerts into coordinated action.”
Overall, this architecture reduces fragmentation, clarifies roles, and helps your team respond faster to evolving threats across networks and services.
The Core Layers of CSMA You Need to Know
Focus on four foundational layers that convert telemetry and identity into coordinated controls. These layers form the operational backbone of any effective cybersecurity mesh architecture and help you turn central intent into local action.
Security analytics and intelligence: unify data, detect faster, trigger response
Unify data from endpoints, cloud services, email, and networking to spot anomalies sooner.
When analytics link signals across platforms, automated playbooks can isolate threats and reduce manual steps. That improves detection fidelity and lowers false positives.
Distributed identity fabric: adaptive access, directory services, and entitlement
Identity is the anchor. A distributed fabric enforces adaptive access, proofing, and entitlement checks wherever users and assets live.
This reduces risky over‑permissioning and keeps least privilege consistent across systems.
Consolidated policy and posture management: translate and orchestrate policies
Central policy must become actionable. Consolidated policy management translates plain‑language rules into tool‑specific configs or runtime authorization.
That alignment cuts drift, fewer misconfigurations, and smoother audits.
Consolidated dashboards: complete visibility for quicker, coordinated actions
Composite dashboards give teams one pane of glass to prioritize incidents and coordinate response.
“A single operational view turns scattered alerts into decisive, coordinated action.”
- Better detection fidelity
- More reliable enforcement across assets
- Lower administrative overhead for platforms and teams
Key Benefits and Capabilities for Your Organization
A composable security approach turns scattered products into a single operational advantage for your teams.
Reduce complexity and close interoperability gaps
Consolidated visibility and policy shrink operational drag while your teams keep using the security tools they already trust.
Integrating best‑of‑breed products cuts deployment times and reduces configuration failures. That saves time and lowers risk when you add services or partners.
Strengthen protection, detection, and response
Sharing intelligence across platforms raises detection fidelity and lowers false positives.
One signal can trigger coordinated actions elsewhere, so a single incident does not cascade into multiple attacks. This aligns with NIST functions to protect, detect, and respond.
Increase agility and operational resilience
A shared identity and policy fabric helps you onboard new services faster without manual rework.
Interoperable platforms prevent single points of failure and speed recovery. The result: faster initiatives, better compliance readiness, and measurable time savings in operations.
- Fewer blind spots and improved posture across assets
- Shorter mean time to detect and respond
- Simplified audits with centralized evidence
“A coordinated fabric of identity and intelligence helps you detect and respond faster across hybrid environments.”
How to Implement a Cybersecurity Mesh in the Present Landscape
Start with visibility and a clear plan. Start by mapping every asset and identity to reveal where your sensitive data really lives. That inventory covers cloud tenants, on‑prem systems, endpoints, and remote users.
Centralize policy management so you write rules once and translate them into each product’s native controls. This reduces drift and speeds compliance.
Integrate tools via APIs and event sharing so detections and blocks propagate across networks and services. Automate enrichment, correlation, and containment where it matters.
Operationalize with unified dashboards, shared threat intelligence, and runbooks. Clear governance assigns ownership to operations, SecOps, and platform teams.
- Inventory assets, identities, and data flows to prioritize gaps.
- Standardize policies centrally, then map to each tool.
- Automate cross‑tool enforcement and alerts.
- Measure progress using NIST KPIs: protect, detect, respond.
“Begin with identity and policy, add analytics for faster detections, then expand integrations to cover email, web, endpoint, and network.”
Where Cybersecurity Mesh Meets Zero Trust and AI
When identity and data labels drive decisions, least privilege becomes practical across clouds and on‑prem systems.
Enforcing least privilege with identity- and data-centric policies
You can enforce least privilege by tying access to identity and data sensitivity. Use labels to mark sensitive files and link those labels to conditional access rules.
That makes policy portable: controls follow the user, the app, or the document no matter which platform hosts them.
Coordinated detection and response powered by AI and machine learning
AI analyzes signals across email, endpoint, web, and networks to spot multi‑stage attacks earlier.
Machine learning reduces false alerts and recommends playbook actions. When threats appear, automated actions can block, contain, and speed response across products and services.
Designing an open, interoperable system of systems for sustained zero trust
Build with open APIs, standards, and integrations so your architecture stays flexible as new platforms arrive.
Interoperability ensures your organization can combine best‑of‑breed tools without vendor lock‑in. That keeps verification continuous and practical for users with adaptive MFA and conditional checks.
“Verify explicitly, use least privilege, and assume breach” — align these zero trust pillars to operational controls for faster, measurable outcomes.
- Identity-driven rules enforce consistent access and reduce risks.
- AI ties signals together to speed detection and automated response.
- Open integrations preserve flexibility as technology and threats evolve.
Conclusion
Start with clear policy and identity controls so management becomes purposeful and measurable across your environments.
This approach lets you centralize intent while local tools enforce rules where users and data live. It reduces complexity and keeps your teams focused on high‑value work.
Plan a pragmatic roadmap: map assets and identities, standardize policy, add analytics and dashboards, then integrate key tools. Use KPIs to show progress and brief leadership with concrete examples from your stack.
By prioritizing data, identity, and interoperable management, your organization can improve posture, speed response, and scale protections without rip‑and‑replace. CSMA becomes a practical architecture that helps enterprise teams manage risks in the cloud era.